“Boot camp” style fitness classes are increasingly popular, but not all boot camps are created equal. When comparing fitness classes, the most important thing to look for is a track record of real people getting real results.
At Fit Body Boot Camp, our fitness classes are not “classes” in the traditional sense but results-driven, high-energy sessions focused on weight loss and body toning.
Fit Body Boot Camp is not like your typical gym or fitness center. Every workout session is professionally designed and led by our nationally certified coaches, who are driven to help you get the results you want.
At Fit Body Boot Camp, we welcome all fitness levels. Our friendly certified coaches and positive community will be sure to support and motivate you throughout your weight loss journey.
Our signature Afterburn workouts combine High-Intensity Interval Training (HIIT) with Active Rest Training to produce 30-minute workouts that burn twice the calories in half the time and keep the metabolism running at a higher rate for up to 36 hours post-workout.
Compare our 30-minute sessions to other fitness classes, which typically last 45 minutes to an hour. With our Afterburn workouts, you don’t need to choose between results and convenience — you can have both!
Research shows that shorter, more intense fitness classes (HIIT) and workouts that activate one set of muscles while others rest (Active Rest) lead to faster and more sustainable weight loss. It turns out, what’s best for your schedule is also best for your health.
Best of all, our 30-minute sessions are scheduled throughout the morning and evening to fit your schedule!



Our group fitness classes begin with one simple question: How could we make the powerful results of 1-on-1 personal training available to more people?
The answer: provide the benefits of 1-on-1 training by keeping the same high quality while splitting the cost among 20-30 people per session. The key to that is our certified fitness coaches — who are basically the ultimate version of personal trainers.
They go beyond the basics of instructing a fitness class — they provide the personal accountability you need to reach the body of your dreams and keep it for good.
Our fitness coaches are experts at creating weight loss results and keeping you safe and motivated both on the floor and off the floor. They don’t stop at correcting form and demonstrating exercises — they get to know you.
They learn your unique strengths, challenges, goals, and desires. They help tailor YOUR fitness classes to your own lifestyle and needs. Even when you leave boot camp, they’re available through email and Facebook to provide healthy tips and inspiration.
Our fitness coaches strive to make every boot camp session the best 30 minutes of your day — and they also recognize that the other 23 ½ hours of your day still count! That’s why they’ll even check in outside of boot camp to help you stay on track with your diet and healthy lifestyle.
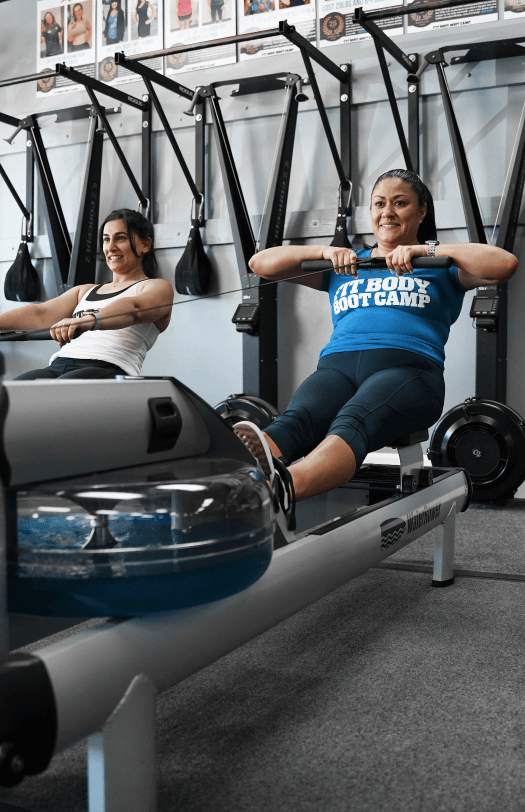


While many fitness classes operate outdoors, we recognized early on that this leaves your workout open to way too many interruptions. An outdoor fitness class can be shut down at any moment by anything from bad weather to city restrictions on public spaces.
When we took the boot camp fitness class indoors, we took it one step further. We realized we had an opportunity to create a welcoming space and community — a home away from home.
We recognize the courage it takes to commit to a fitness journey. That’s why we’re committed to maintaining a trendy, clean, modern space where you can bond with others on that same journey.
When you walk into a Fit Body Boot Camp, you’ll recognize in an instant that it’s more than just a fitness class. It’s a place where we recognize and celebrate each other’s victories. It’s a place where we donate to the causes that matter most to us.
It’s YOUR place to meet positive, like-minded people who will hold you accountable to your dreams and motivate you every step of the way.
When you first walk into a Fit Body Boot Camp, you’ll notice right away that it’s a completely different setup than any other gym or fitness class. There’s no confusing heavy equipment. In fact, there’s not even any equipment that plugs into the wall.
All you see is simple, safe equipment that anyone can use. With the expert guidance of our fitness coaches, that’s all you need for a challenging,fat-torching workout!
See, our workouts are built around bodyweight and resistance training and specifically tailored to be “Low Risk, High Reward.” Unlike other fitness classes that borrow effective but potentially dangerous exercises from pro athletes and bodybuilders, we keep things simple and safe.
At Fit Body Boot Camp, we do one thing, and we do it better than anyone else: we deliver weight loss results. There are no gimmicks — just our science-backed Afterburn workouts led by passionate fitness coaches committed to your success!

One of the most important aspects of losing weight and unwanted fat outside of working out, is what you’re eating. We even say that the most important personal training happens in the kitchen, although not all gyms or personal trainers are ready to admit this! At Fit Body Boot Camp, we’re fully committed to your fat loss results, and that means we bring the same science-backed, lifestyle-friendly approach to your diet that we bring to our workouts.
We do NOT enforce calorie counting, restrictive dieting, crash dieting, or quick-fix “cleanses” that actually do the body more harm than good. It’s common for our members to eat more food after they sign up, not less. You might be asking yourself, “how is that possible?” Well, as it turns out, most problems relating to weight gain and poor health come from malnutrition which means you’re not getting enough REAL food. For that reason, we embrace a whole-food diet that gives you the power to express yourself and delight your family with a huge variety of tasty, fat-torching meals.


"Since my joining, my physical, mental and emotional health have improved. My recovery from having my third son was so much smoother than after my first two, which I attribute largely to Fit Body. My strength came back more quickly and for the first time, I had zero signs of postpartum depression. Wherever you are at in your fitness journey, I highly recommend giving MV Fit Body Boot Camp a try!"
Kimberly Ziaei | Mission Viejo, California
Mission Viejo, California

“If you are looking for an awesome, inclusive, fun, place to work out THIS IS IT! Fit Body is a fantastic place, the coaches are knowledgeable, fun and they push you and motivate you, no matter your fitness level you’ll feel challenged in every class. The classes are always different so you’ll never ever get bored.”
Maria Espinoza | Berkley, Michigan
Berkley, California

“Berkley Fit Body is AWESOME. When the boot camp style gym I previously went to closed, I was devastated and never thought another gym would compare. Not only does Berkley Fit Body meet the expectations set by my previous gym, it significantly exceeds them and provides me things I never knew I needed!”
Amber Chinoski | Berkley, Michigan
Berkley, California

"At my heaviest point and most unhealthiest, I decided to give this gym a try after a recommendation. I am SO glad I did! We are all a family and support each other 110%. No judging. I've learned how to eat healthy, have gotten incredibly strong, lost over 55 pounds, and am happy to stay in the best shape of my adult life.”
Kathy Llewellyn | Whitesboro, Texas
Whitesboro, Texas

“I was really hesitant when I signed up 2 months ago. I did not think I would enjoy the workouts and honestly had no clue if it would make a difference in my life. I was COMPLETELY wrong. Thanks to Fit Body, my body is slowly changing for the better and my confidence levels are growing. I honestly couldn't think of a better place/environment to help better your body and mind!”
Maegan Hess | Fern Creek, Louisville
Fern Creek, Louisville

“I am approaching my 2 years there at Fern Creek Fit Body. I have a BAD knee and thought I would try the place. I LOVE THIS PLACE. This place is for all people at all different levels of what each individual can do in a work out. I have lost some weight and I have built my confidence. Most of all I have a new extended family. Not only the staff but other members are always welcoming, helpful and encouraging.”
Dana Ballinger | Fern Creek, Louisville
Fern Creek, Louisville

“When I first started in November of last year, I had high blood pressure, high cholesterol, and I was pre-diabetic. I constantly felt tired, suffered from headaches almost everyday, and absolutely hated doing anything active because my back and my joints always hurt. Now, at almost 40, my energy level is better than it was in my 20s, my blood pressure is in the normal range and I’m no longer pre-diabetic. I recommend Fit Body to anyone and everyone who’s looking to make a positive change in their lives!!”
Penelope Melko | Sioux Falls, South Dakota
Sioux Falls, South Dakota
Fit Body Boot Camp is a fitness franchise dedicated to transformation. 30 minutes per session is all it takes to help you reach your weight loss goals.
Fill out the form below to connect with your local Fit Body about how you can get started.